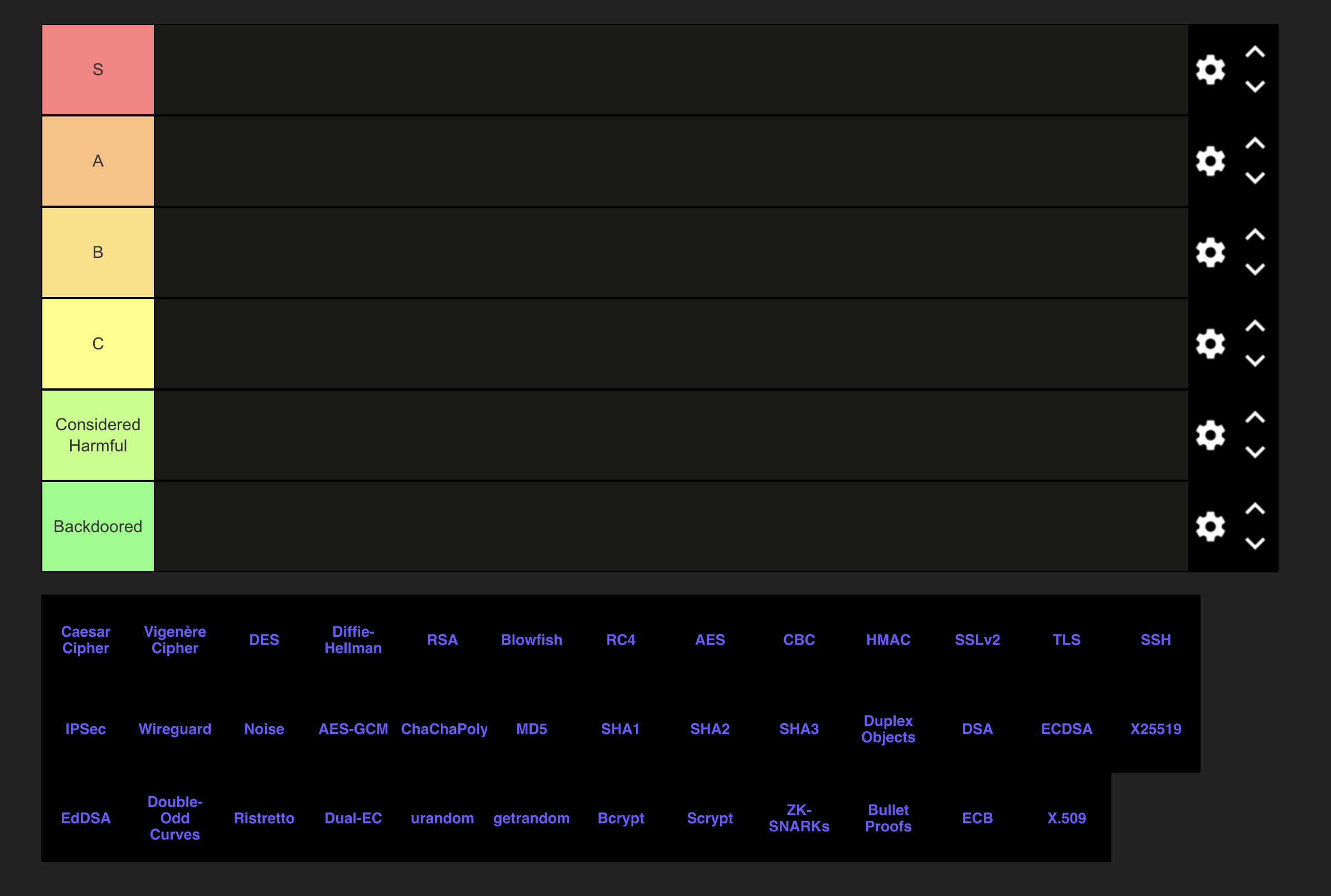
Bonus episode! The AI presidents create a cryptography tier list. Play along at home and make your own tier list here.
This episode is definitely not safe for work (NSFW) and definitely a parody. Do not base your decision in the 2024 election off of this podcast episode. No campaigns have endorsed this podcast.
This transcript has been edited for length and clarity.
O: Alright guys, let’s do this. We all ready for a cryptography tier list?
B: Yeah let’s fucking do this.
T: Obama this is a bad idea. Bad idea. But people are saying I’m the best at tier lists so let’s go.
O: OK. We’re starting with some classic. First up is the Caesar cipher.
T: If the Caesar cipher is so great, how come he got stabbed? I like people that don’t get stabbed.
B: Leave Brutus out of this Donald! The caesar cipher was a great innovation for it’s time and accomplished its goal of securing communication between Caesar and his generals.
O: I don’t know Joe, it is just a fixed-key substitution cipher after all.
T: It’s backdoored.
O: It is not backdoored, it’s just lame.
B: It’s not for computers, it’s for regular hard working Americans.
T: Sleepy Joe is so old he only likes the ciphers that don’t require computers.
B: Fuck you Donald, let’s see you try to default the Huns.
O: Shut up you two. I’m marking it as Considered Harmful and that’s that.
O: Next up is a similar one, the Vigenere cipher
B: That wasn’t actually invented by Vigenere.
O: That’s right it was invented by an Italian
T: I don’t care, they’re all losers and suckers. It’s a dogshit cipher defeated by frequency analysis.
B: You can’t deny it’s better than the basic caesar cipher donald
O: I’m tired of talking about all this stuff from before Claude Shannon was even born. I’m putting it in C tier, one above the Caesar cipher. Let’s get to some more modern ciphers, like DES.
T: DES is dogshit. It was backdoored by GCHQ.
O: What the fuck, Donald? GCHQ make DES stronger by editing it to be resistant to differential cryptanalysis years before the existence of differential cryptanalysis was declassified.
B: He’s absolutely right Donald, I was there.
O: Wait, how old are you?
T: You can’t honestly be telling me you’re using DES, it only has 64-bit blocks. Even if the S-boxes weren’t dogshit the whole thing is too close to the birthday bound on modern connections.
B: Who’s birthday is it?
O: It’s not anybody’s birthday.
B: Trump said it was close to someone’s birthday.
O: No he didn’t
T: Of course Obamna likes DES, he bailed out the banks and all the banks use 3DES
O: If the banks used better cryptography maybe I wouldn’t have had to bail them out. DES was impressive at the time, but it is a bad choice in modern times. I’m marking it as Considered Harmful.
O: How about Diffie-Hellman? Seems like an easy S-tier.
T: Wrong! We have to split out the elliptic curve Diffie-Hellman and the finite field Diffie-Hellman. Finite field Diffie-Hellman was not a good deal. Elliptic curves are a better deal.
B: What the hell is he talking about?
O: Fine, we can drop finite field Diffie-Hellman to A-tier.
O: Next up is RSA.
B: S-tier
T: Sleepy Joe is so old he still thinks RSA is a good idea. Have you ever tried padding an RSA ciphertext Joe? RSA is C-tier at best.
B: You set the padding bytes to the number of bytes. Folks, it’s that simple.
T: PKCS my ass Sleepy Joe
O: Would you cut it out you two? RSA certainly is impactful but we really should have listened to Rogaway in the 90s about PKCS vs OEAP.
T: Blichenbacher is gonna fuck you up Joe
B: Anyone can tell you not to use e=3 Donald
T: No the other Blichenbacher
O: There are a lot of Blichenbacher attacks. I can’t keep track of them all.
T: C-tier
B: S-tier
O: I’m splitting the difference and putting it B-tier, even though Shamir and Koblitz are both going to kill me.
B: This is crap.
O: Shut up Joe.
O: OK next up is Blowfish
T: Blowfish? We’re talking about Blowfish?
B: Is that the porn star you slept with?
T: You just hate me because I’m cool and rich and you’re old, sleepy Joe
O: It’s a cipher from Schnier
B: Didn’t he come to the White House when you and I were president?
O: I don’t know, probably. He just does policy now.
T: I can’t believe this cipher is even here. It was cool for two minutes in the 90s.
B: Like Oasis
T: Sleep Joe gets it.
O: Yeah, it was fine, but there’s really no reason to use it these days. C-tier.
O: The RC4 stream cipher is next, that should be an easy considered harmful.
T: Good call Obamna, RC4 is totally broken. If you use RC4, China can read all your plaintext like they have a golden key.
B: Trump knows all about golden streams.
O: Hah, Good one Joe!
B: Thanks Obama
O: OK, AES should be an easy S-tier.
T: What the fuck Obama AES is too underspecified to be S-tier. To do anything with it you have to use a fancy cipher mode, it doesn’t work out of the box like the ciphers from DJB.
B: Who is DJB
T: He’s the best cryptographer.
O: What, why are we talking about DJB?
B: I’ve never heard of him.
O: Everyone has heard of DJB. But I don’t think we should be putting him on a pedestal, he’s said some crazy shit and hangs out with bad people.
B: Like Trump’s mom!
O: Exactly Joe.
T: What the fuck obama
O: Be quiet Donald. It’s fair to say AES needs to be used in the proper mode to be safe. I think that’s more NISTs fault, but I’ll put it in A-tier.
O: Speaking of modes, CBC is up next.
B: CBC is all you need to encrypt as much as you want.
T: Once again Sleepy Joe doesn’t understand how to implement secure padding. Are you really using CBC mode Joe?
B: You can do random access decryption, what’s not to like.
T: What’s not to like? It’s called padding oracles Joe.
B: Skill issue!
O: I agree with Trump, we have better options these days Joe.
B: HMAC the ciphertext and it’s all fine.
O: No one does that, everyone does Mac then encrypt.
B: Who does Mac then encrypt.
T: TLS does that Joe, that’s why it’s dogshit. Remember Poodle?
B: Shut the fuck up Donald. Wait, what do dogs have to do with this?
O: Both of you shut the fuck up. CBC is C-tier.
B: Trump said there was a Poodle.
O: POODLE is a padding oracle attack on CBC mode in SSLv3.
B: Then where is the dog?
T: Obama is hiding the dog.
O: No I’m not, what the fuck are you two talking about. I’m moving on.
O: HMAC is up next.
B: That shit is S-tier for sure.
T: Sleepy Joe, have you never heard of an AEAD. I bet this guy has never heard of an AEAD. What are you using HMAC for?
O: Donald has a point. HMAC is great, but you don’t need to use it if you’re able to use an AEAD like AES-GCM. I’ll knock it down to A-tier.
B: HMAC is core to KEM-DEM Barack
O: Everyone stopped using KEMs until we got to post quantum Joe
T: Joe is so old he’s still using an abacus
B: 64k of RAM should be enough for anybody
O: Speaking of old stuff, we’ve got SSLv2 up next.
B: What happened to SSLv1
O: You’d have to ask Marc Andressen that
T: I’ll ask Peter Thiel
O: What, why would you ask Peter Theil, he wasn’t at Netscape in the 90s
B: I was in Wilmington in the 90s
T: He’s my favorite venture capitalist.
O: This doesn’t have to do with VCs or a16z. This is about Netscape.
B: I got Netscape off my AOL CDs. Does anyone need minutes?
O: Minutes? How do you still have minutes?
B: I bought 40 years worth of minutes in 98, and I’m still working through them.
O: I can’t believe this. I’m putting SSLv2 in Considered Harmful because its handshake is vulnerable to MITM.
T: Those third-rate developers at the fake news organization OpenSSL left it enabled by default for too long and gave us DROWN. SSLv2 is a garbage protocol.
B: OpenSSL has done more for encrypted communications than any other software package in the world.
T: Remember Heartbleed Sleepy Joe? Disastrous, gross incompetence. Worst library ever.
B: After Heartbleed we were able to get them funding and they really improved the quality.
O: That’s true. But OpenSSL 3.0 has been a mess.
O: Anyway, I’m putting SSLv2 in Considered Harmful and TLS in S-tier. It’s goated.
B: I agree, TLS is fucking goated.
T: S-tier? Really? Has our society degraded so much that this is what counts as S-tier. Does nobody remember 2015 when there was a new TLS attack coming out every month. I won’t deny it’s better than SSLv2 but S-tier should be reserved for things that created a revolution in cryptography.
O: Brink of a revolution? You wouldn’t even put Diffie-Hellman in S-tier. How is TLS not the foundation of the web revolution?
B: Just put it in S-tier Barack. Don’t give him a chance, he’ll talk your fucking ear off. And besides, the only revolution he knows about was January 6th.
T: Shut up Sleepy Joe, I’ll tell you exactly how not. It may be used for HTTPS but that’s the only reason it’s popular. Cryptographic agility was a terrible decision. It isn’t until TLS 1.3 that they even bothered to define the groups for key agreement in advance. Who wants to waste a round trip just to pick a prime number that might be backdoored.
B: L take
O: The protocol has evolved over time. TLS 1.3 could be considered a whole entry on its own.
B: Yeah, how come SSLv2 gets its own entry in the tier list but TLS 1.3 doesn’t?
T: The only people who run TLS 1.3 are liberal big tech and they use 0-RTT to push their fake news even faster. No one else implements it.
B: Skill issue
O: Fine. TLS did have its over time, but I think we landed in a good place with TLS 1.3. I’ll move it down to A-tier.
B: I can’t believe TLS is fucking A-tier.
T: Deal with it Sleepy Joe
B: Fuck you Donald
O: OK, SSH. This one should be another easy S-tier.
B: I agree but I’m sure Donald is going to come in with some contrarian bullshit
T: SSHv2 was the only protocol designed in the 90s that wasn’t pure scum. I agree it’s S-tier.
O: Holy shit we agreed on something. Let’s keep this moving with some VPN protocols. How do we feel about IPsec?
B: I’ve been deploying IPsec VPNs for years. It’s a secure way to bridge your on-prem and cloud networks.
O: Wait, you do network security architecture consulting?
T: Yeah, and I don’t know why he does. Sleepy Joe’s network diagrams are going to ruin this country and your networks will be overrun with crime. Everyone knows IPsec is a dogshit protocol.
O: IPsec is very complicated compared to a more modern VPN like Wireguard.
B: Wireguard? Are you kidding me? No one can deploy anything beyond a simple point-to-point Wireguard network without using Tailscale unless you have a full blown network platform team like fly dot io.
T: That’s true Sleepy Joe
O: Fine. IPSec is C-tier and Wireguard is A-tier.
B: I can’t believe you would do this to me Barack
O: Can we just rank the Noise protocol framework?
T: It’s easy to make a protocol framework secure if you leave out key distribution. I would rather roll my own with libsodium.
O: You shouldn’t roll your own crypto Donald
T: I’m not rolling my own crypto, I’m using libsodium.
B: I’ve never heard of Noise.
O: How have you heard of Wireguard and not Noise? Wireguard uses Noise under the hood.
T: Nothing uses Noise under the hood, it’s all custom variants.
O: That’s the point Donald, it’s a protocol framework, not a protocol implementation or specification.
T: That’s fucking useless Obama
O: It popularized triple diffie-hellman and can provide authentication without needing signatures. And many systems have other mechanisms for key distribution, like an IdP.
T: It’s a B-tier framework that sidesteps the hard problems.
B: What’s a protocol framework Donald
O: Shut up Joe.
O: Fine, I’ll put it in B tier even though that feels mean to Trevor Perrin.
O: Next up are AES-GCM and ChaChaPoly
T: GCM is trash. ChaCha all the way.
O: Of course you’d say that Donald, you’re such a DJB-stan.
B: I thought his initials were DJT—Donald J Trump
O: No Joe that doesn’t make any sense. You can’t stan yourself.
T: I can because I am the best and I am always winning.
B: How come you lost the election to me then Donald
T: You stole all the votes in Michigan. Nothing can be done to cure that giant scam now.
B: Loser
O: Shut up you two. AES-GCM is good when you have hardware support. ChaCha is good when you need to encrypt in software.
T: Fuck you Obama, GCM is a trash AEAD and it’s vulnerable to nonce collision attacks.
O: So is ChaCha you idiot. I’m ranking both B-tier because they involve caller managed nonces.
B: I just use a counter.
T: Of course you do Sleepy Joe.
O: Donald weren’t you just complaining about the birthday bound? Shouldn’t you prefer counter-based systems.
T: I never said that. Fake news.
O: God damn it not this again.
B: Would you just shut up man
D: Winning
O: We’re moving on to hash functions.
T: Dank Biden knows all about the good hash
B: That’s right I’m fucking lit
O: Joe you gotta share that with me. Anyway, first one up is MD5. This is an easy Considered Harmful, it’s literally in the name of the paper.
T: Remember when they used all those PS3 to calculate a hash collision of a Root CA?
B: That was totally dope. Also I love the PS3.
T: Me too Joe. Want to play Journey later?
O: You can’t pick who you play Journey with, that’s the whole point of the game.
T: Joe can watch me play it.
B: Yeah, we can switch off Barack.
O: If we’re playing PS3 I want to play The Last of Us.
T: You’re just bandwagoning because of the TV show
O: Fuck you donald. Also, what the fuck does any of this have to do with MD5?
T: Why are we even bothering with MD5. it’s a total fraud, a bigger fraud than Biden winning the election.
B: Skill issue
O: Donald stop saying that.
T: SHA1 is also a total fraud.
B: There’s online tools to collide PDFs. It’s even weaker than Trump’s wall.
O: Donald should have hired the team behind SHA2 to build his wall, maybe then it’d be collision resistant.
T: No I should have hired DJB to make my wall because the only hash function I trust is SipHash. Attacks only get better, and if SHA1 is broken then SHA2 and SHA3 must be next.
O: That’s now how attacks work Donald. And SipHash isn’t even on our list. Stop bringing DJB into this.
T: NIST backdoors all the standards. I don’t want anything that came out of a NIST competition. I told Rick Perry to cut NIST but he forgot what department they were in.
B: NIST competitions grow the economy. Benefits everybody. Hurts nobody.
O: Oh fuck, I forgot about Rick Perry. He was a total idiot.
B: We have to ignore this clown Obama. SHA-2 is clearly S-tier.
O: Agreed. What about SHA-3?
B: There’s a SHA-3?
O: Yes Joe, there’s a SHA-3. It’s a sponge-based construction.
T: Moon math, I don’t trust it.
O: Sounds like a skill issue.
B: What is a sponge construction.
O: It’s good for making duplex objects, but to be honest, there’s not a big reason to not just use SHA2 for regular hashing. I’m putting it in B-tier.
O: Since nobody knows what a duplex object is except me, I’m putting them in A-tier, because they’re amazing but I’m not sure if they’re quantum-resistant.
T: Quantum computers aren’t real. They’re fake news.
B: Isn’t quantum for key distribution.
T: Quantum key distribution isn’t real sleepy joe
O: Donald’s right about quantum key distribution. It’s a scam.
O: Let’s move on to some signatures. How do we want to rank DSA and ECDSA?
B: I don’t see the point of DSA when you have RSA.
T: RSA Joe? Are you so out of touch you think we should still sign with RSA?
O: We already ranked RSA Donald. But if you can’t handle RSA signatures, I’ve got bad news for you about the web PKI.
T: I don’t care about the Failing Web PKI Obama. But DSA is D-tier shit. It wasn’t useful until DJB invented elliptic curves.
O: DJB didn’t invent elliptic curves, it was Koblitz and Miller.
T: Never heard of them.
B: Elliptic curves are just too complicated.
T: Skill issue!
O: I’m putting DSA in C-tier and ECDSA in A-tier.
T: I’ll allow DSA in C-tier because of it’s impact, but what are you smoking that you think ECDSA is A-tier? Do you just expect everybody to special-case points being added to themselves in addition and somehow still be constant time. Edwards curves are so much better, ECDSA is B-tier at best.
O: That may have been true in the 2000s, but we have complete formulas for the NIST curves now with no special cases.
T: Yeah, and they work by converting the loser NIST curves to them to Edwards representations.
O: OK, fine. ECDSA is B-tier. But since no god damn Ed25519 libraries can interoperate with each other on the edge cases, I keeping EdDSA at B-tier as well.
T: I’ll allow it so long as you make Curve25519 S-tier.
O: If Curve25519 is S-tier, how come everybody has to copy Adam Langley’s implementation everywhere?
B: Who’s Adam Langley? Is he the guy from Maroon 5 that looks like a Chipotle bag?
O: No, that’s Adam Lambert. Agl is a cryptographer at Google.
T: Want to get Chipotle later Joe?
B: Oh fuck yeah, that sounds awesome Donald. Obama, hurry up with the tier list, Donny and I are gonna get Chipotle.
O: God damn it, I’m not the one holding everything up. I’m putting Curve25519 in A-tier because of the library and API issues, and I’m putting the Double Odd Curves in S-tier because they’re clearly better than 25519.
T: No one takes those curves seriously, but whatever. I’m beyond caring about your terrible tier-list.
O: I don’t know why I agreed to do this either, but we’re here and we’re going to finish it. Next up is Ristretto.
B: If you need a prime order group, why don’t you just take the integers mod p?
O: That’s order p-1 Joe
B: Oh
T: Ristretto is great because it lets you bridge Curve25519, the best curve, to cryptocurrency protocols that use zero-knowledge proofs.
O: I’m not sure I care about that use case that much, but I agree it’s very good at what it does and Joe already showed us it’s easy to fuck this up. I think this is a great example of do one thing and do it well, let’s put it in S-tier.
T: You just want to rank it higher than Curve25519 to fuck with me, but if that’s what it takes to get some acknowledgement of all the developments in cryptography that have been driven by investment in cryptocurrency, I’m fine with it.
O: Next up is Dual-EC
T: Backdoored!
B: We don’t know that.
O: I mean, we basically do Joe. Ask me about it on Signal. It’s going in Backdoored.
O: Next up is /dev/urandom for generating random numbers.
T: Backdoored!
O: It’s not fucking backdoored Donald. The implementation is open-source.
B: What if the entropy pool has been fully initialized yet? Remember all those keys Nadia factored using gcd back in 2012? Joe Biden remembers.
T: Backdoored!
O: Shut the fuck up Donald. It’s not backdoored. Joe, sounds like you’re making the case for getrandom, which fixes the initialization blocking issue with urandom.
B: Yeah, OpenBSD has this right from the start.
T: Shut up Joe, Theo might hear you and then we’ll have to invite him to Chipotle.
O: Can I come to Chipotle?
T: No, you have Ligma.
O: I do not have Ligma.
B: Ligma balls.
T: Sleepy joe gets it.
O: Fuck both of you. I’m putting urandom in B-tier and getrandom in S-tier. Looks like Bcrypt and Scrypt are next.
T: I know you don’t respect law and order, but if SHA2 is S-tier then Bcrypt also should be S-tier.
O: Finally, Donald says something reasonable. How else are you going to hash passwords?
B: You’re supposed to hash passwords?
T: Not if you use email to sign in Joe.
B: I always just reset my password because I can’t remember it.
O: I’m putting Scrypt in B-tier because no one actually needs a memory hard hash.
T: What about Dogecoin?
O: Donald, I know you’re an Elon-stan but Dogecoin is fucking stupid.
T: Not, it’s fucking goated.
B: It has a picture of a Shiba Inu, it’s fucking goated.
O: Stop fucking saying fucking goated. Can we just finish this tier list?
O: Actually, you know what. I don’t understand any of this zero knowledge crap. If anything is moon math, it’s SNARKs.
B: I agree, anything with an elliptic curve is moon math.
T: That’s not what he said Sleepy Joe. ‘ B: Doesn’t matter, I still agree that SNARKs are moon math.
O: Let’s skip ZK-SNARKs and Bullet Proofs. That leaves us with ECB and X.509.
B: ECB is the one with the penguins right. It’s the worst of the cipher modes.
T: Finally, Sleepy Joe says something I can agree with. Put ECB considered harmful.
O: Done. That leaves us with X.509.
T: Trash
B: Trash
O: Trash
O: It’s considered harmful.
T: We did it Joe, let’s go get Chipotle while my Minecraft is updating.
B: Yeah, let’s do it.
Sign off noises
O: Why do I hang out with those two?
Sign off


![Campaign Security with [REDACTED]](/images/voting-booth.jpg)